How to Ensure Your Recovery System Is Truly Ready for an Attack
In today’s reality, where cyberattacks occur almost daily, data recovery has become one of the pillars of any cyber defense strategy. Many organizations believe that snapshots — those “moment-in-time” images of their data — will save them when disaster strikes.
But when the real moment comes, and the system must actually recover, many discover that their seemingly healthy snapshots are completely unusable.
This is one of the most dangerous silent failures in the IT and cybersecurity world — a false sense of security.
The Illusion of Safety: Why a Snapshot Is Not a Backup
A snapshot allows you to roll back to a specific point in time, but it is not a true backup. While backups are stored separately and include dedicated recovery procedures, a snapshot is part of the same storage or virtualization system.
If that system is compromised, infected, or damaged — your snapshots go down with it.
The problem is that most organizations don’t realize this. They see hundreds of available snapshots and assume they’re “protected.” In reality, they’re relying on copies that may be corrupted, infected with ransomware, or simply not recoverable.
In other words, it’s like keeping the keys to your house inside the house — and then realizing the door is locked from the outside.
Why Snapshots Fail During Recovery
1. Hidden Contamination:
Advanced ransomware operates silently. Files may already be infected days or weeks before encryption occurs. Every snapshot taken during that period contains the same malicious code.
2. Infrastructure Dependency:
If the storage or virtualization environment itself (such as vCenter or NetApp) is compromised, snapshots stored within it may be inaccessible.
3. Inconsistent States:
Not all snapshots are created while the system is in a stable state. If data writes or updates occur during the capture, the snapshot may contain partial or inconsistent data.
4. Lack of Testing:
Many teams never perform a real recovery test. They verify that the snapshot “exists” — but never test restoring a full, working environment. The result: a false sense of readiness that collapses under pressure.
The Solution: Snapshot Validation
To ensure that a snapshot can actually be restored, organizations need a validation process — a continuous, automated check that confirms integrity, cleanliness, and recoverability.
This is where CyberSnap comes in. It doesn’t just check if a snapshot exists — it verifies if it’s usable, clean, and accessible.
The process includes:
- Integrity Verification: Ensuring all data is intact, complete, and readable.
- Intelligent Analysis: Detecting anomalies, encryptions, or suspicious changes inside the snapshot.
- Automated Sandbox Testing: Restoring the snapshot into an isolated environment to confirm it boots and operates correctly.
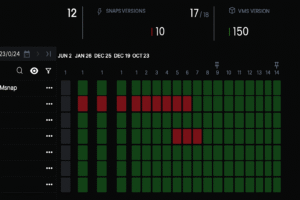
- Readiness Reports: Automated reports that show which snapshots are safe to restore — and which need attention.
This gives organizations real visibility into what can be recovered, how long it will take, and which copies are compromised — before disaster strikes.
Step-by-Step: How to Ensure You’re Truly Ready
- Map Your Snapshots: Identify all snapshots across core systems, including timestamps, frequency, and storage locations.
- Perform Regular Restores: Conduct a full recovery at least once per quarter — not a simulation, but a live environment test.
- Separate Storage Layers: Keep snapshots independent from the production infrastructure to avoid single points of failure.
- Automate Validation: Deploy tools that continuously verify the health and consistency of your snapshots.
- Involve the Cyber Team: Recovery isn’t just an IT concern — it’s a core part of cyber resilience planning.
Real-World Example
A mid-sized financial organization suffered a ransomware attack. The team rushed to restore their latest snapshot — but the restore failed.
An investigation revealed that every snapshot taken in the previous two weeks was already encrypted.
The company was forced to revert to older backups, losing two weeks of critical transaction data and facing five days of downtime.
Afterward, they implemented automated snapshot validation to continuously test and verify snapshot integrity. Since then, they’ve known exactly which copies are clean, which are compromised, and how quickly they can recover.
Final Thoughts
Saying “we have snapshots, we’re safe” is no longer valid.
In an era of sophisticated ransomware, organizations must validate, test, and continuously monitor their recovery readiness — just like any other critical security control.
Snapshot Validation changes the rules: it transforms recovery from a gamble into a measurable, controlled, and reliable process.
Organizations that test themselves during peace time — are the ones that recover during crisis.
CyberSnap ensures that when that day comes, you can truly restore with confidence.