The problem
Your Snapshots May be Hiding the Threats You’re Trying to Escape
Ransomware, malware, and corruption can infiltrate storage systems, silently embedding themselves into your Snapshots. When you try to recover, they strike encrypting, stealing, or destroying your data. Without knowing if your Snapshots are truly safe, recovery becomes a dangerous gamble.
Experience Unmatched Storage Security and Data Usability from One

CyberSnap Threat Detection®
Uncover Hidden Threats Inside Your Data
Go beyond storage vendors’ external protection. We detect ransomware, malware, and other threats deep within your data, ensuring complete security.

CyberSnap Usability Verifier®
Ensure Your Data is Always Ready for Use
Verify the usability of Snapshots, VMs, and applications in real time, making sure they are fully operational and corruption-free.

CyberSnap Platform®
Comprehensive Data Security and Operational Assurance
The CyberSnap Platform offers a single, cohesive solution that combines both threat detection and usability verification for complete data resilience.
Maximizing Business Value with CyberSnap
CyberSnap enables you to protect your critical assets while minimizing risk, allowing you to operate with confidence.
Enhance your existing storage with deep threat detection and data usability, ensuring your data, VMs, and applications are always operational and secure.
Automate data usability verification, minimizing manual labor and freeing up IT resources to focus on strategic tasks, all while reducing costs.
Automatically detect and isolate threats within your storage environment, ensuring your business stays secure without interruptions or disruptions.
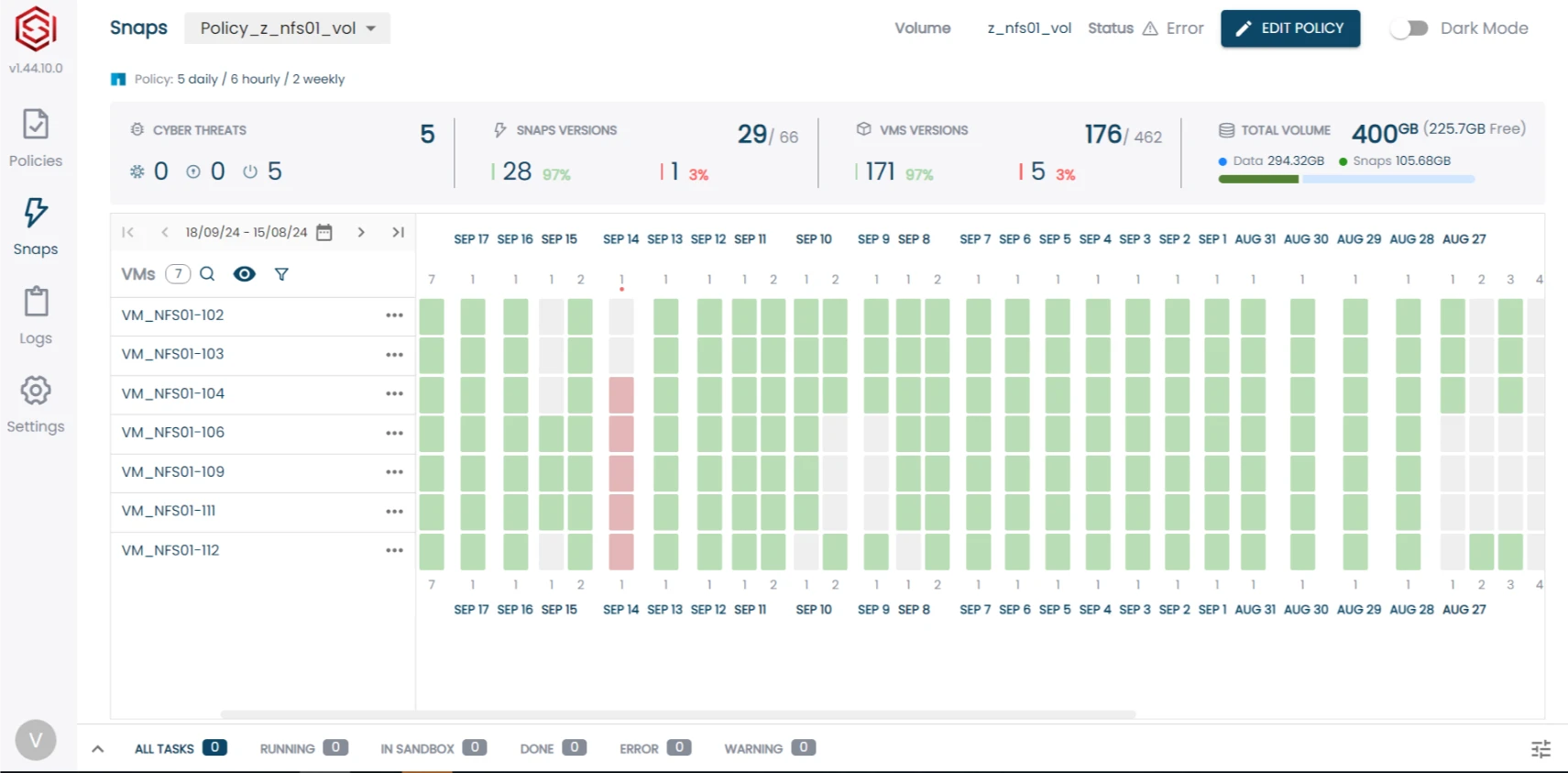
Visualize Data Security Like Never Before
Gain full visibility into your storage environment with real-time threat detection and data usability tracking. Our intuitive map instantly shows the status of your VMs and Snapshots, highlighting potential risks and ensuring everything remains secure and operational.